PDF Encryption to Reduce Forwarding Risk 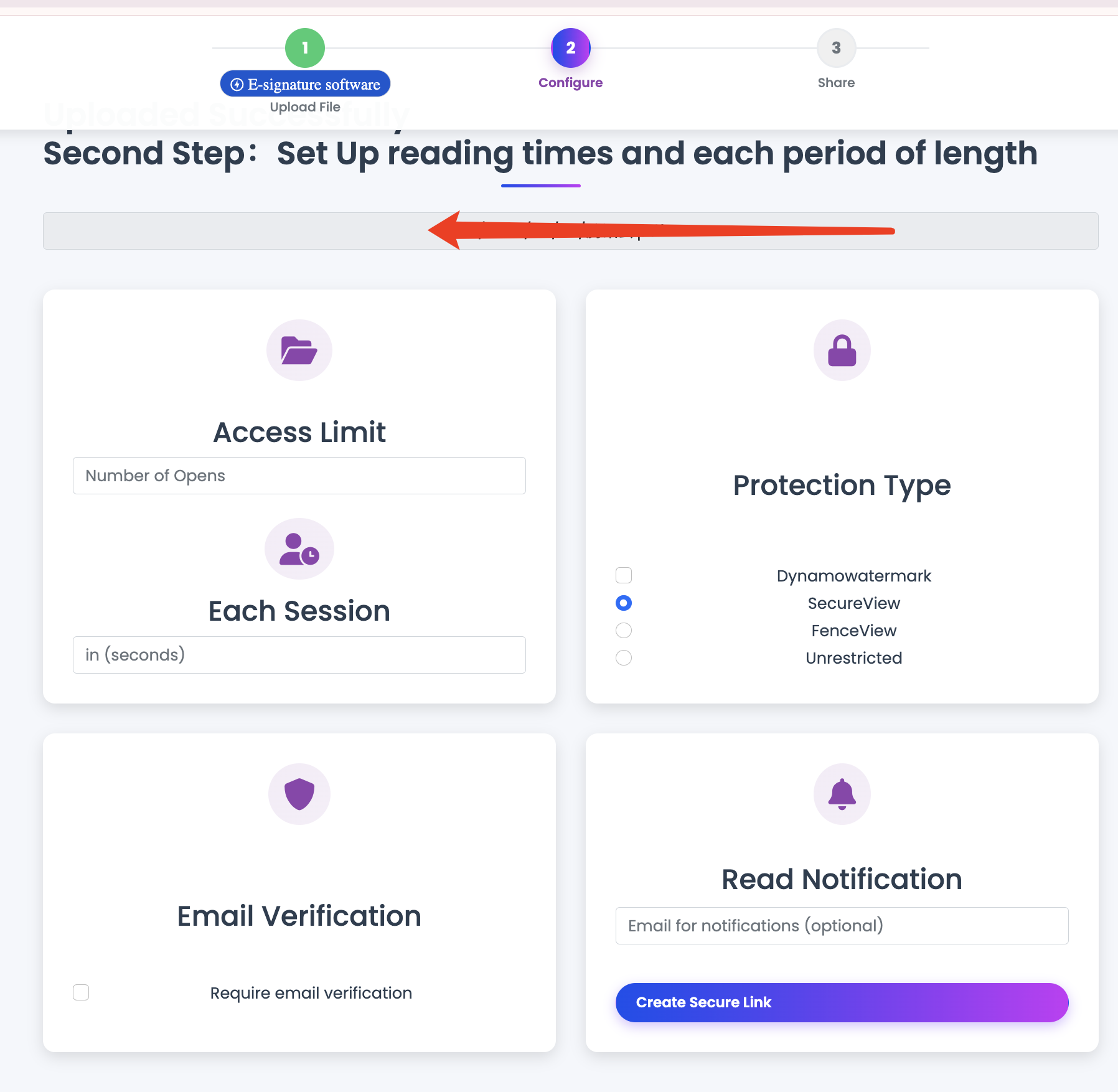
PDF Encryption to Reduce Forwarding Risk
Encryption alone is not enough. Forwarding risk is managed by combining access controls, short lifecycles, and response playbooks.

Layered protection model
- Protected access for sensitive docs
- Download restrictions for review-only files
- Expiry windows for temporary visibility
- Open limits to cap uncontrolled spread
- Visitor ID watermark for accountability
Practical policy templates
Proposal / commercial draft
- Download: off
- Expiry: 7-14 days
- Open limit: medium
Legal/financial document
- Download: off
- Expiry: 3-7 days
- Open limit: low
- Watermark: on
General reference document
- Download: on
- Expiry: optional
- Open limit: high
Incident response steps
- Disable leaked link.
- Issue a new link to approved recipients.
- Review open logs and timing.
- Tighten policy for next distribution cycle.
Final takeaway
Think in layers, not features. A small, repeatable policy stack is more effective than complex one-off settings.